From Vulnerable to Vigilant: How Layered Cybersecurity Protects What Matters Most
Guest post from Greater Rochester Chamber member LMT Technology Solutions
Cybersecurity begins with Culture and Leadership
Relying on a single cybersecurity measure is like defending a castle with just one wall. Cyber threats are more sophisticated than ever, and while tools like antivirus and firewalls are essential, they are no longer sufficient on their own.
A true layered cybersecurity model begins with Culture and Leadership. From the top down, security must be a mindset - not just a toolset. Security Awareness Training must be practical and relevant, policies and processes must be clear and consistently applied, and leaders must model the behaviors that reinforce a security-first approach.
Technology is only one layer. The most crucial layer is the people who use it. When culture and leadership serve as the vessel for layered security, the entire organization becomes more resilient, proactive, and prepared for threats that continue to grow in sophistication. This is where layered cybersecurity isn't just beneficial, it's critical for business survival.
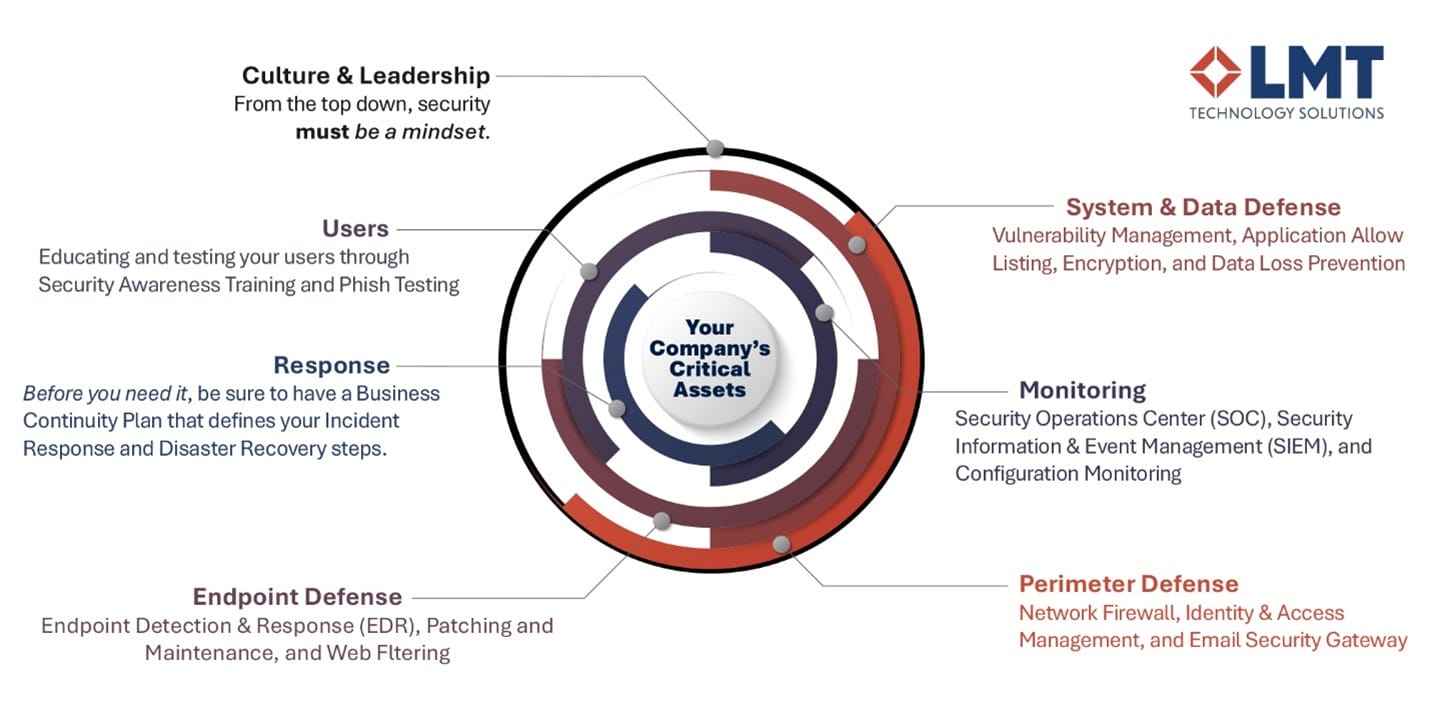
What is Layered Cybersecurity?
Layered cybersecurity is a multi-layered defense strategy that combines technology, processes, and people to protect your organization from evolving threats. Instead of relying on a single solution, each layer - firewalls, antivirus, training, policies, and culture - works together to detect, prevent, and respond to attacks, keeping your business secure from every angle.
Building Your Layers
A robust layered cybersecurity strategy typically includes a combination of:
- Culture & Leadership: From the top down, security must be a mindset.
- Perimeter Defense: Network Firewalls, Identity & Access Management, Email Security Gateway
- System & Data Defense: Vulnerability Management, Application Allow listing, Encryption & Data Loss Prevention.
- Endpoint Defense: Endpoint Detection, Response Patching, Maintenance, Web Filtering
- Users: Multi-factor authentication, strong password policies, least privilege access, security awareness training, phish testing.
- Monitoring: Security Operations Center (SOC), Security Information & Event Management (SIEM), Configuration Monitoring
- Response: Business Continuity Plan, Incident Response, Disaster Recovery, Back-ups.
Don't wait until a breach exposes your vulnerabilities. LMT Technology Solutions specializes in building comprehensive, adaptive, and resilient security layers tailored to your business risks. Contact LMT Technology Solutions today and discover how we can design your layered defense strategy to protect against sophisticated threats and secure your digital future.
